In September 2017 AWS have added AWS Network Load Balancer to it’s portfolio of load balancing services. NLB offers great performance and a unique set of features, however it is also distinctly different to the Application Load Balancer (ALB) or it’s multi-purposed predecessor – the Elastic Load Balancer (rebranded as the ‘Classic’ Load Balancer)
- It is an extremely scalable Layer 4 load balancer
- It currently only supports TCP traffic load-balancing
- It preserves source IP and port
- It does not support direct assignment of Security Groups, unlike ELB/ALB
- Provisions a single ENI/IP in each AZ
- Can be used in conjunction with the PrivateLink service to allow interesting cross-account connectivity patterns.
The last two features/characteristics provide interesting possibilities when designing connectivity to application workloads deployed in AWS.
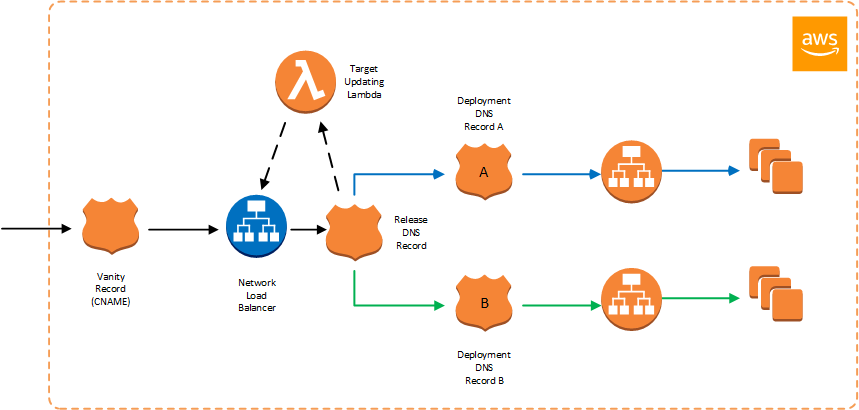
Use Case #1 - Static IP address for blue/green deployment
Working with a client, we were facing restrictions due to the security architecture patterns adopted by the enterprise. Connectivity between on-premises infrastructure and AWS was established with DirectConnect but was limited to a small number of predefined flows, identified by a set of source and destination IP addresses and ports.
Despite these constraints the application teams were looking to leverage blue/green methodology for application deployment with ability to re-deploy the entire application stack with almost immediate roll-back to a previous version using low TTL DNS records.
Taking a lead from an excellent blog article from AWS on “Using static IP addresses for Application Load Balancers” we leveraged NLB’s static IP assignment characteristic, by deploying a persisted load balancer as part of the application on-boarding. The NLB was configured with a supporting lambda that was used to dynamically update targets for the NLB based on the DNS record assigned to the target load balancer.
In doing so, This allowed us to use fixed static IPs provided by the NLB to “front” a highly dynamic workload while staying within the bounds of the established enterprise security architecture pattern, with minimal firewall changes in the perimeter.
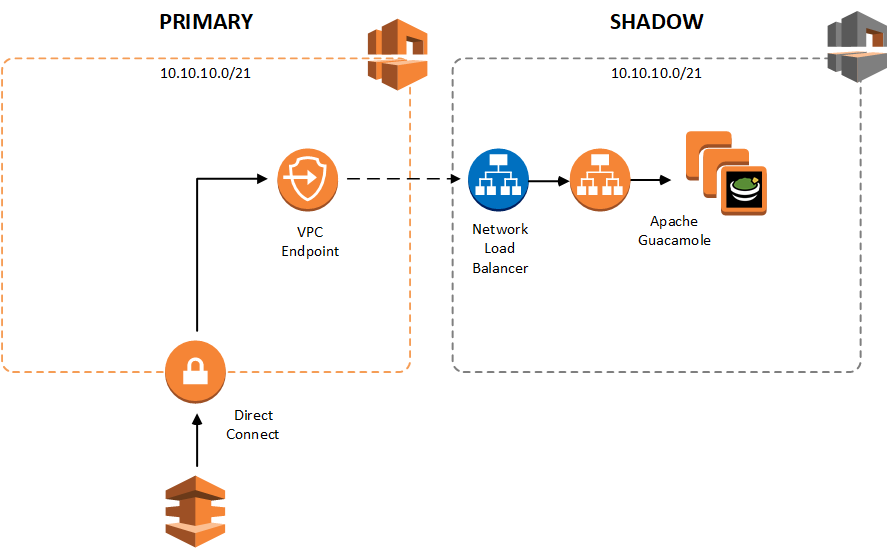
Use Case #2 - Providing remote access into an isolated environment
The second scenario utilised the NLB ability to function as a VPC Endpoint Service and assisted in providing direct connectivity into an isolated infrastructure development environment.
Working with an enterprise client our team was able to fully automate deployment of the AWS core infrastructure required for the foundation platform, including accounts, network, IAM and compliance configurations for the entire environment. To avoid any possibility of clashes with existing production/non-production environments, the core infrastructure was tested using a set of parallel (shadow) accounts completely disconnected from the client’s network.
Although the majority of testing was automated and did not require direct VPC connectivity, the infrastructure developers still required access to the shadow environment for troubleshooting and manual sanity checks.
To enable this connectivity, we deployed a set of Apache Guacamole remote desktop gateway hosts to the testing accounts. A Network Load Balancer was then used to expose the Guacamole application as a VPC endpoint in the existing non-production accounts. This allowed infrastructure developers to establish connectivity into an environment with overlapping CIDR ranges without significant network isolation effort or additional cost of maintaining parallel DX connectivity.
Note: With the release of the New Session Manager some of the requirements of this use case may be addressed, however more complex connectivity patterns such as use of RDP for connectivity to Windows hosts or use of SSH tunneling may still require an alternative means of connectivity such as this)
Conclusion
The AWS Network Load Balancer is an excellent service with some really interesting and useful features which may be used in tackling some interesting enterprise challenges. It does however have it’s drawbacks such as lack of support for UDP traffic and no support for direct attachment of Security Groups, however like all AWS services, we will continue to keep an eye on its additional capabilities as it matures.